Industry Guide
Application Fraud
Learn more about the growing threat of application fraud — and how financial institutions can prevent it
On This Page
What Is Application Fraud?
Application fraud is a form of identity fraud in which a criminal applies for a financial product, such as a credit or debit card, account or credit line with no intention of ever paying back the lender.
What Is the Difference Between First-Party and Third-Party Application Fraud?
Application fraud can take two forms:
First-party application fraud
A fraudster applies for a financial product using their actual personal details and then either uses it to convert credit into cash or maxes out their cards with no intention of ever repaying. Although it is possible to commit first-party application fraud when applying for a loan, it’s far less common because loan applications typically require identity verification, which lowers fraudster’s success rate.
Third-party application fraud
A fraudster applies for a loan or line of credit using a stolen or synthetic identity. Third-party application fraud can be more challenging for financial institutions to detect than first-party application fraud because fraudsters are able to easily acquire or generate new identities and abandon old ones before they’re caught.
What Is Credit Card Application Fraud?
Credit card application fraud is a form of application fraud in which a criminal uses either their actual identity, a stolen identity or a synthetic identity to apply for a line of credit. Once approved, the fraudster will then either convert their credit into cash using bank checks or max out their credit card — all before severing contact with the financial institution without having ever repaid.

Most first-party application fraud falls under the category of credit card application fraud because it’s much easier for criminals to use their actual credentials to apply for new lines of credit than it is to apply for a loan.
Credit card application fraud not only harms financial institutions, it affects consumers as well. If a fraudster uses a stolen identity to commit credit card application fraud, the consumer may default on a debt they’re not even aware they’re carrying, which can damage their credit score.
What Is Loan Application Fraud?
Loan application fraud is a form of application fraud in which a criminal either their uses actual identity, a stolen identity or a synthetic identity to apply for a loan without any intention of repayment.
Most third-party application fraud falls under the category of loan application fraud because loan applications typically require identity verification, making it harder for criminals to use their actual personal information to apply. Synthetic identities, however, are much harder to trace and can be easily generated and discarded as needed.
What Are Synthetic Identities?
A synthetic identity is what you get when a fraudster combines actual, stolen credentials with fabricated personally identifiable information in order to create a new identity.
The most common method of generating a synthetic identity is to steal an actual person’s credentials — often those of a child, an unhoused person, a recent immigrant, an incarcerated individual, an elderly person or the recently deceased — from government documentation and combine it with fabricated details, such as a false address and phone number. For this reason, synthetic identities are considered a form of identity fraud.
In 2020 alone, financial institutions lost an estimated $20 billion to synthetic identity fraud.
Although this approach to creating synthetic identities — known as partial or patchwork identity fabrication — is by far the most common, some fraudsters may craft identities out of whole cloth in what’s known as total identity fabrication.
Third-party application fraud can be especially difficult to detect because there is no immediate victim. Unlike other forms of identity fraud, in which a customer is more likely to report fraudulent activity on their account, fraudsters using synthetic identities can easily discard old identities and create new ones without financial institutions noticing. In 2020 alone, financial institutions lost an estimated $20 billion to synthetic identity fraud.
What Is Bust-Out Fraud?
Bust-out fraud is a sophisticated fraud strategy in which a group of criminals — often an organized crime ring — commits multiple acts of application fraud at the same time, using multiple stolen or synthetic identities.
Credit card application fraud is the preferred method of bust-out fraud, as criminals will work in concert to build their credit over time, making their activities look more legitimate to financial institutions and enabling them to increase their credit or even open additional lines of credit using the same credentials. Then, when the time is right, the criminals will max out all of their cards simultaneously and disappear.
What Is Checking and Savings Account Fraud?
Checking and savings account fraud is a form of application fraud in which a criminal applies for a checking or savings account under false pretenses, using stolen or synthetic credentials. Once approved for an account, the criminal then uses it to commit various types of fraud, including check fraud, deposit fraud and money laundering. In almost all cases, the fraudster ends up depleting the account of funds before abandoning it — again, without repaying — and moving on to their next scheme.
How Does Application Fraud Occur?
Application fraud doesn’t just happen overnight — it typically takes some time for fraudsters to put all the pieces in place and execute their plan. Most application fraud schemes follow the same basic structure, which breaks down into the following stages:
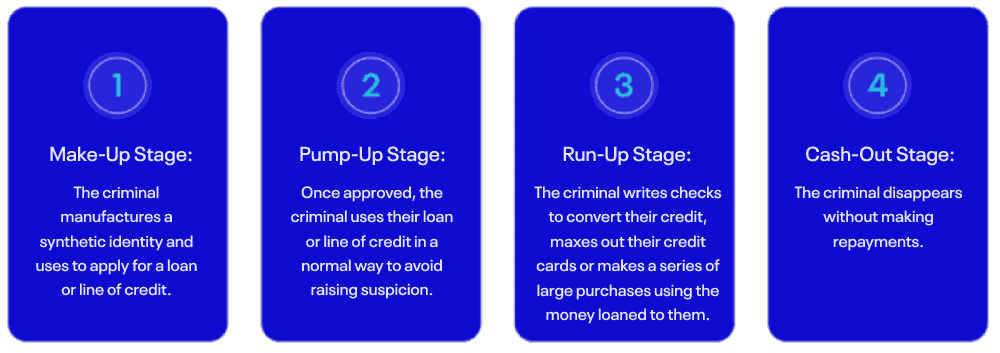
The criminal manufactures a synthetic identity to use in their scheme. It’s important to note that this stage is not always included in the application fraud lifecycle, as a criminal might opt to use their actual personal information or stolen credentials to apply for a loan or line of credit rather than a synthetic identity.
Fraudsters will often test a financial institution’s risk controls at this stage of the process, submitting multiple applications — sometimes up to 20 or more — and slightly tweaking details each time until they receive approval.
For example, a criminal might say that they’re a software engineer and ask for a credit limit of $10,000 on one application and say that they’re a sales manager and ask for a credit limit of $5,000 on another. The purpose of this is to see which identities get rejected and which ones get approved, as it provides valuable context to how much risk a financial institution is willing to tolerate and what kind of customers it’s looking for.
Once the criminal has identified weakness within a financial institution’s approval process, they will continue to exploit it to get as many applications through as possible.
Once the criminal has been approved, they use their loan or line of credit in a normal way, so as not to make the financial institution suspicious of their intentions. In the case of credit card application fraud, the pump-up stage is also an opportunity for fraudsters to give financial institutions the false impression of good credit so that they can request additional credit.
In the case of credit card application fraud, this is when the criminal either writes themselves multiple checks in order to convert their credit into cash or maxes out their credit cards. In the case of loan application fraud, this is when the criminal starts to make large purchases using the lender’s money.
At this stage of the process, criminals will often make bad payments to clear their balance and access new funds. So, for example, if an account had a $15,000 spending limit, the fraudster might max out their spending, then make a bad payment to clear that balance and then quickly spend an additional $15,000.
When the bad payment inevitably bounces and the criminal moves on to the cash-out stage — also known as bust-out — the financial institution is left with an account with a $15,000 limit, but a $30,000 balance.
The fraudster disappears without a trace, leaving the financial institution at a loss.
What Channels Do Fraudsters Typically Use To Commit Application Fraud?
There are many channels through which criminals are able to gain access to stolen credentials for fraudulent purposes, including (but not limited to):
- Data Breaches
The second quarter of 2022 alone saw approximately 52 million online data breaches; although this number was down by 56% compared to the previous quarter, that’s still 52 million opportunities for fraudsters to gain access to individuals’ credentials and personal information. Given the massive quantities of data available and the frequency of data breaches, it’s little wonder that they’ve become a popular access point for criminals looking to commit application fraud. - Call Center Attacks
Call and contact centers have become a common attack vector in recent years, with criminals using social engineering and other sophisticated methods to access customers’ personal information — information they can then use to apply for lines of credit or loans in customers’ names.
52 Million
online data breaches in the second quarter of 2022
1 in 10
adults aged 65 or older experienced identity theft in 2020
- Intercepted Mail
Even in a world where the vast majority of communications take place online, physical mail remains a vulnerability that would-be fraudsters can easily exploit. In the United States, criminals have taken advantage of the United States Postal Service’s Informed Delivery program, which enables consumers to digitally preview incoming mail. Fraudsters can sign up for the program using their target’s actual address and a false name, see when their target is due to receive a new credit card in the mail and intercept it before it can reach the intended recipient. - Senior Scams
Senior citizens are a popular mark for fraudsters looking to commit identity theft; in fact, nearly one in 10 adults aged 65 or older experienced identity theft in 2020, with financial losses totaling $2.5 billion. Once they’ve secured identifying information, criminals can then use these credentials to apply for loans and lines of credit in senior citizens’ names. - Social Engineering
Social engineering — which encompasses a wide range of attacks, including phishing, smishing, whaling and scareware — is one of the most common means for criminals to gain access to people’s personally identifiable information. Research from Positive Technologies indicates that this attack vector, which relies heavily on psychological manipulation, accounts for 57% of all attacks on organizations, and 90% of all attacks on individuals.
Fraudsters are also able to leverage advanced tools and technology to execute application fraud attacks — tools such as:
- Web Scraping Software
Perhaps a fraudster’s most essential tool, web scraping software makes it easy for criminals to extract personal information from web pages, which they can then use to create synthetic identities. - Bots
Criminals can use computer programs known as bots to generate hundreds of email addresses across popular mail servers and attach those email addresses to synthetic identities. - Device Emulators
A computer program designed to simulate the virtual environment of another computer or device, device emulators were originally created to enable developers to test out application functionality on different devices. In the hands of fraudsters, they’re a dangerous tool; Criminals can use device emulators to avoid authorization tools and other detection software. - Device Obfuscation
Device obfuscation involves using different masking techniques — including virtual machines and mobile device flashing — to make a single device appear as though it’s many different devices. This tactic then enables fraudsters to apply for multiple lines of credit or loans from the same device without triggering financial institutions’ detection systems. - IP Obfuscation
Similar to device obfuscation, IP obfuscation is a masking technique that enables criminals to conceal their IP addresses, making it easier for them to circumvent IP blacklists and financial institutions’ fraud prevention systems.
How Pervasive Is Application Fraud?
Application fraud poses a serious and fast-growing risk to financial institutions around the world. CoreLogic’s National Mortgage Application Fraud Risk Index, which is an aggregate of individual loan application fraud risk scores, rose from a reading of 125 in Q3 ‘21 to 138 in Q4 ‘21 — an increase of 10.4% — indicating a substantial increase in the risk of loan application fraud.
According to research from the Aite Group, market forces have stoked application fraud growth, causing application fraud attack rates to increase by approximately 16% per year. Application fraud has become so prevalent that fraud executives report synthetic identities resulting from application fraud, first-party check/deposit fraud resulting from application fraud and first-party lending fraud (including credit card and loans) resulting from application fraud as the top-three attack patterns that concern them most.
What Risks Does Application Fraud Pose to Financial Institutions?
The most obvious risk application fraud poses to financial institutions is that fraudsters apply for loans, credit cards and other lines of credit and then accept funds without any intention to repay, leading to a substantial loss of funds for financial institutions.
To put things into perspective, the Aite Group reports that synthetic identity fraud losses — which “[account] for the lion’s share of losses associated with application fraud” — are projected to reach more than $4.1 billion by 2023.
Application fraud has an impact on banking customers, too. Although fraudsters aren’t necessarily stealing from customers’ personal accounts, they are using customers’ personal information to apply for lines of credit — and when they default on those payments, it can take a serious toll on customers’ credit. With that in mind, it’s imperative that financial institutions prioritize application fraud prevention and detection not only to protect themselves, but also to ensure a positive customer experience.

What Can Financial Institutions Do To Combat Application Fraud?
There are many application fraud prevention measures financial institutions can take to protect themselves, including:
- Closely monitoring all application data to see whether the same information or the same device is reused across multiple otherwise unrelated identities
- Requiring loan and credit card applicants to provide additional identity documentation, such as a driver’s license or voter registration, to verify that they’re a real person and receive approval
- Develop a robust Know Your Customer (KYC) framework — including a customer identification program, customer due diligence and enhanced due diligence — to maintain KYC compliance and ensure that anyone submitting an application is who they claim to be
- Applying machine learning algorithms and behavioral analytics to determine the likelihood of an application being fraudulent
- Automating authentication — two-factor authentication, multi-factor authentication and more — using machine learning and artificial intelligence
- Investing in application fraud detection solutions that combine network intelligence with community fraud signals for deeper insights
Featured in the Federal Reserve’s fraud mitigation providers service showcase, ACI Fraud Management for Banking is a best-in-class solution that enables financial institutions to turn fraud prevention — including application fraud prevention — into a competitive differentiator.
When used in conjunction with our Fraud Scoring Services, proprietary network intelligence technology and advanced machine learning models, it enables financial institutions to stop application fraud in its tracks, so they can focus on optimizing their customer experience.