3d secure guide
3D Secure Authentication: The Complete Guide
Builds an additional layer of security into the payments process
On This Page
Research has shown that more than two billion people purchased goods or services online,1 and global retail eCommerce sales have grown by more than 25%.
The total number of card-not-present (CNP) transactions has likewise increased; with a 9 percent compound annual growth rate, CNP transactions are on track to overtake card-present transactions.2
Although convenient, these transactions introduce additional risk to the payments process: Without the card or cardholder physically present, it is far more challenging to authenticate the transaction. According to a study from Juniper Research,3 merchants are projected to lose approximately $130 billion USD to CNP fraud between 2018 and 2023.
As eCommerce continues its meteoric ascent, merchants must implement stronger fraud and identity theft prevention methods. 3D Secure authentication is a security protocol that enables merchants to safeguard online transactions and comply with the EU Revised Directive on Payment Services (PSD2) strong customer authentication standards.
What is 3D Secure Authentication?
3D Secure authentication — also known as 3DS or payer authentication — is a security protocol designed to reduce the risk of fraud, identity theft, and other illicit activities during CNP transactions. 3DS gets its name from the fact that it is based on a three-domain model; each domain refers to one of the parties involved in the authentication process:
- Acquirer domain: The bank or merchant to which money is being paid
- Issuer domain: The cardholder’s issuing bank
- Interoperability domain: The underlying systems that support 3DS
At a high level, 3DS authentication works by sending Extensible Markup Language (XML) messages over Secure Sockets Layer (SSL) connections with client authentication. This process creates a digital certificate that verifies the identities of the different parties involved in the transaction.
Arcot Systems (now CA Technologies) developed 3D Secure authentication in 1999, and Visa was the first major card scheme to bring it to market in the form of Visa Secure in 2001. As noted, 3DS has gained popularity in recent years for its ability to support PSD2 compliance.
Originally adopted in 2015 and fully implemented in 2019, PSD2 is a European regulation that ensures electronic payments are more secure, creating a more integrated European payments market. As such, PSD2 includes a strong customer authentication (SCA) standard, which stipulates that multi-factor authentication (MFA) must be applied to all electronic payments to ensure secure transactions. 3DS authentication satisfies PSD2’s SCA requirement, which led to widespread adoption of the protocol. Today, multiple card schemes offer their own branded version of 3DS, including Mastercard Identity Check, Discover Global Network ProtectBuy, and American Express SafeKey.
What is 3D Secure Authentication 2.0?
Despite its initial success, 3D Secure authentication faced numerous complaints from consumers, largely due to its incompatibility with different devices and mobile browsers. These complaints were justified: Given that it was invented in 1999, the original iteration of 3DS was never designed to accommodate mobile devices and platforms. As it began to decline legitimate transactions at an increasing rate, it became apparent that 3DS required an upgrade.

In 2018, EMVCo — a consortium between Visa, American Express, Mastercard, China UnionPay, Discover, and JCB — introduced 3D Secure 2.0. Compared to 3DS 1.0, 3DS 2.0 includes a software development toolkit that supports native integration with mobile applications. Additionally, rather than require consumers to complete authentication steps at checkout, with 3DS 2.0, issuers’ Access Control Server (ACS) platforms conduct risk-based and biometric authentication in the background, entirely out of sight. Consumers only need to provide additional authentication information if the ACS platform detects a high risk.
Ultimately, 3D Secure authentication 2.0 is designed to deliver a consistent customer experience across all platforms and devices, enhance payment orchestration, and create frictionless flows, while allowing for a better overall consumer experience. According to research from Visa, 3DS 2.0 is expected to reduce checkout times by 85% and cart abandonment by 75%. In addition to reducing fraud risk, 3DS 2.0 shifts liability for 3DS transactions to the issuer, eliminating chargebacks.
Updates to 3DS 2.0 have introduced additional enhancements. 3DS 2.1 increased the number of data elements that merchants can send to issuers at the point of transaction to 100. By accessing richer datasets, issuers assess potential risk at a more rapid rate, further optimizing frictionless flow. Updates included in 3DS 2.2 enable merchants to request exemptions through their acquirer, issuers to use third parties for delegated authentication, and users to conduct authentication outside of the main authentication flow.
How Do 3DS and 3DS 2.0 Authentication Work?
As noted, 3D Secure authentication confirms the identities of the different domains involved in an electronic transaction by using XML messages, SSL connections, digital certificates, and client authentication.
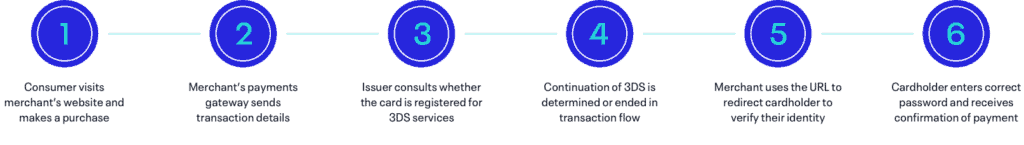
At a high level, a typical 3DS 1.0 flow looks something like this:
- A consumer visits a merchant’s website and enters their card information at checkout when they’re ready to make a purchase.
- The merchant’s payments gateway automatically sends transaction details and a 3D Secure verification request to the cardholder’s issuing bank.
- The issuer consults its internal records to determine whether that card is registered for the 3DS service.
- If the card is enrolled in 3DS, the issuer will send a verification response to the merchant, along with a URL to its ACS platform; if the card is not enrolled in 3DS, the merchant will receive an automated message notifying them, at which point they must decide whether to carry on without 3DS or end the transaction flow.
- The merchant uses the URL to redirect the cardholder to the issuer’s ACS platform, where they will be prompted to verify their identity; common identity verification methods include entering a unique password, answering a security question, fingerprint identification, bank app approval, and using a URL sent via SMS on the cardholder’s phone.
- If the cardholder provides the correct password or security answer, they are redirected to the merchant’s website for payment confirmation.
Though this process helped increase payments security, it was not without flaws. In addition to experiencing compatibility issues, many consumers are frustrated over the extra step in the payment process, while others question the authenticity of 3DS pop-ups and/or redirects. Both scenarios increased cart abandonment, prompting certain regions to eliminate 3D Secure authentication4 and instead conduct their internal fraud screenings.
Similarly, consumers with multiple cards began to favor issuers who did not require authentication. To compete for wallet share, many issuers started to adopt Dynamic 3DS, a version of 3DS in which only high-risk transactions are redirected for authentication. Given that 3DS shifts chargeback liability from merchants to issuers, the widespread adoption of Dynamic 3DS resulted in fewer fraud screening tactics amongst merchants, which led to a spike in fraudulent activity. At the same time, with less visibility and intelligence to reference, issuers began to decline transactions at an increasing rate. According to research from Javelin,4 nearly $118 billion USD in revenue was lost in 2014 alone due to false-positive declines in online transactions.
To protect their own best interests, merchants, issuers, and even acquirers had all lost sight of their shared purpose: to mitigate fraud. Therefore, 3DS 2.0 was devised as a means of reestablishing alignment between these various parties and strengthening protections for consumers. Integral to this is the introduction of frictionless flows — that is, authentication flows that take place without additional input from the consumer.

Based on the updated protocol, a 3D Secure authentication 2.0 flow should look something like this:
- A consumer visits a merchant’s website and enters their card information at checkout when they’re ready to make a purchase.
- The merchant’s payment gateway automatically sends transaction details and a 3DS 2.0 verification request to the cardholder’s issuing bank.
- The issuer consults its internal records to determine whether that card is registered for either 3DS 1.0 or 2.0 services:
- If the card is enrolled in 3DS 1.0, it automatically triggers a traditional 3DS 1.0 authentication flow (shown above).
- If the card is enrolled in 3DS 2.0, the issuer initiates a 3DS 2.0 authentication flow (see below).
- If the card is not enrolled in either 3DS 1.0 or 2.0, the flow automatically stops.
- The issuer must determine whether it is possible to complete a frictionless authentication:
- When the issuer identifies a transaction as low-risk and suitable for frictionless authentication, it conducts fraud screening and risk assessment in the background without requiring consumer input.
- If the issuer determines that a transaction is high-risk and frictionless authentication is not possible, it initiates a challenge authentication flow. This operates in much the same way as a traditional 3DS 1.0 authentication flow.
The key distinction between a 3DS 2.0 challenge authentication flow and a 3DS 1.0 traditional authentication flow is that with the former, the cardholder is required to verify their identity using either a one-time authentication code (provided by the issuer) or biometric data.
- The cardholder receives confirmation of a successful payment on the merchant’s website.

In addition to changing the authentication process, 3DS 2.0 ensures all stakeholders have access to and can share richer datasets for more comprehensive fraud screening and risk assessment. These datasets can include up to 100 data points, including a consumer’s geolocation, device ID, transaction history, and more, with a minimum requirement of 20 data points per exchange.
3DS 2.0 also offers greater flexibility by enabling merchants to request transaction risk analysis (TRA) exemption for low-risk transactions. Merchants that receive TRA exemption approval automatically bypass the authentication process. If, however, the issuer sees suspicious activity on the card, it can issue a soft decline, which would prompt the standard 3DS protocol.
Other SCA exemptions5 that apply to merchants that use 3DS 2.0 include:
- Contactless payments at point of sale (PoS): Merchants may bypass the authentication process if the value of the transaction does not exceed €50; the cumulative limit of consecutive contactless transactions without application of SCA does not exceed €150; OR the number of consecutive contactless transactions since the last application of SCA does not exceed five.
- Unattended transport and parking terminals: Merchants may bypass the authentication process for transactions at unattended terminals for transport fares and parking fees.
- Trusted beneficiaries: Merchants may bypass the authentication process if the payer has designated them as a trusted merchant and added them to their issuer’s list of trusted beneficiaries. For a merchant to qualify for this exemption and avoid the application of SCA to future transactions, the payer must first complete an SCA challenge.
- Recurring transactions: Merchants may bypass the authentication process on a series of transactions of the same amount made to the same payee. SCA must be applied either when the series is first set up or to the initial transaction in the series, provided the first transaction is set up by the payee.
- Low-value transactions: Merchants may bypass the authentication process on remote transactions that do not exceed €30, provided velocity limits are met. Additional conditions include that the cumulative limit of consecutive contactless transactions without SCA must not exceed €100, or the number of consecutive contactless transactions since the last application of SCA must not exceed five.
- Secure corporate payments: Merchants may bypass the authentication process on payments made through dedicated corporate processes and protocols.
Why Should You Care About 3D Secure Payments?
3D Secure payments offer substantial benefits to both merchants and consumers, including:
- More secure payments: 3D Secure authentication builds an additional security layer, supporting fraud protection by ensuring that merchants only accept payments from legitimate sources and increasing the total number of data points that stakeholders are permitted to exchange. 3DS 2.0 allows for more comprehensive risk-based authentication.
- An optimized user experience: 3DS 2.0 streamlines the process with faster load times and a smoother interface. It ensures a secure and consistent shopping experience across platforms.
- Increased brand loyalty: 3D Secure authentication prevents consumers’ card credentials from being accessed by unauthorized parties and distributed online; this provides consumers with the peace of mind of knowing that their transactions are hassle-free and secure, which can improve a brand’s reputation with the public, reduce cart abandonment rates, increase sales volumes, and drive customer loyalty.
- Chargeback liability shift: 3DS 2.0 shifts liability for chargebacks due to fraud from merchants to issuers, reducing fees for merchants and safeguarding them from unauthorized transaction chargebacks.
- Enhanced compliance: 3D Secure authentication meets PSD2 SCA requirements, thereby ensuring PSD2 compliance.
What Else Should You Know About 3D Secure Authentication?

Before taking any steps to implement 3D Secure Authentication, there are a few things merchants should know:
- More secure payments: 3D Secure authentication offers an additional layer of security in the payment process, supporting fraud protection by ensuring that merchants only accept payments from legitimate sources and increasing the total number of data points that stakeholders are permitted to exchange. 3DS 2.0 allows for more comprehensive risk-based authentication.
- An optimized user experience: Updates included in 3DS 2.0 make the protocol compatible with all devices and all mobile browsers, while eliminating slow loading speeds and clunky interfaces in the process. 3DS 2.0 offers a consistent and secure shopping experience across devices.
- Increased brand loyalty: 3D Secure authentication prevents consumers’ card credentials from being accessed by unauthorized parties and distributed online; this provides consumers with the peace of mind of knowing that their transactions are hassle-free and secure, which can improve a brand’s reputation with the public, reduce cart abandonment rates, increase sales volumes, and drive customer loyalty.
- Chargeback liability shift: 3DS 2.0 shifts liability for chargebacks due to fraud from merchants to issuers, introducing fees for merchants and safeguarding them from unauthorized transaction chargebacks.
- Enhanced compliance: 3D Secure authentication meets PSD2 SCA requirements, thereby ensuring PSD2 compliance.
An effective 3D Secure payment strategy begins with a profiling solution that provides comprehensive insight into fraud detection. ACI Fraud Management for Merchants offers built-in cost calculation and ROI visualization tools designed to help merchants make more informed decisions.
Contact us today to learn more about this or any of ACI Worldwide’s innovative real-time payment solutions.
Article Sources
- Statista, “E-commerce worldwide – statistics & facts, https://www.statista.com/topics/871/online-shopping/#statisticChapter.” ↩︎
- PaymentsJournal, “CNP in a Post-COVID World – How Businesses Can Prepare, https://www.paymentsjournal.com/cnp-in-a-post-covid-world-how-businesses-can-prepare/.” ↩︎
- Juniper Research, “Retailers to Lost $130bn Globally in Card-not-Present Fraud Over the Next 5 Years, https://www.juniperresearch.com/press/retailers-to-lose-130bn-globally-in-card-not-present-fraud-over-the-next-5-years/.” ↩︎
- Javelin, “False-Positive Card Declines Push Consumers to Abandon Issuers and Merchants, https://javelinstrategy.com/press-release/false-positive-card-declines-push-consumers-abandon-issuers-and-merchants.” ↩︎
- VISA, “Preparing for PSD2 SCA, https://www.visa.co.uk/dam/VCOM/regional/ve/unitedkingdom/PDF/visa-preparing-for-psd2-sca-publication-version-1-1-05-12-18-002-final.pdf.” ↩︎
A Guide to ISO 20022 Implementation Strategies
Get an in-depth look at how banks can adopt and leverage this data-rich messaging standard to drive new revenues